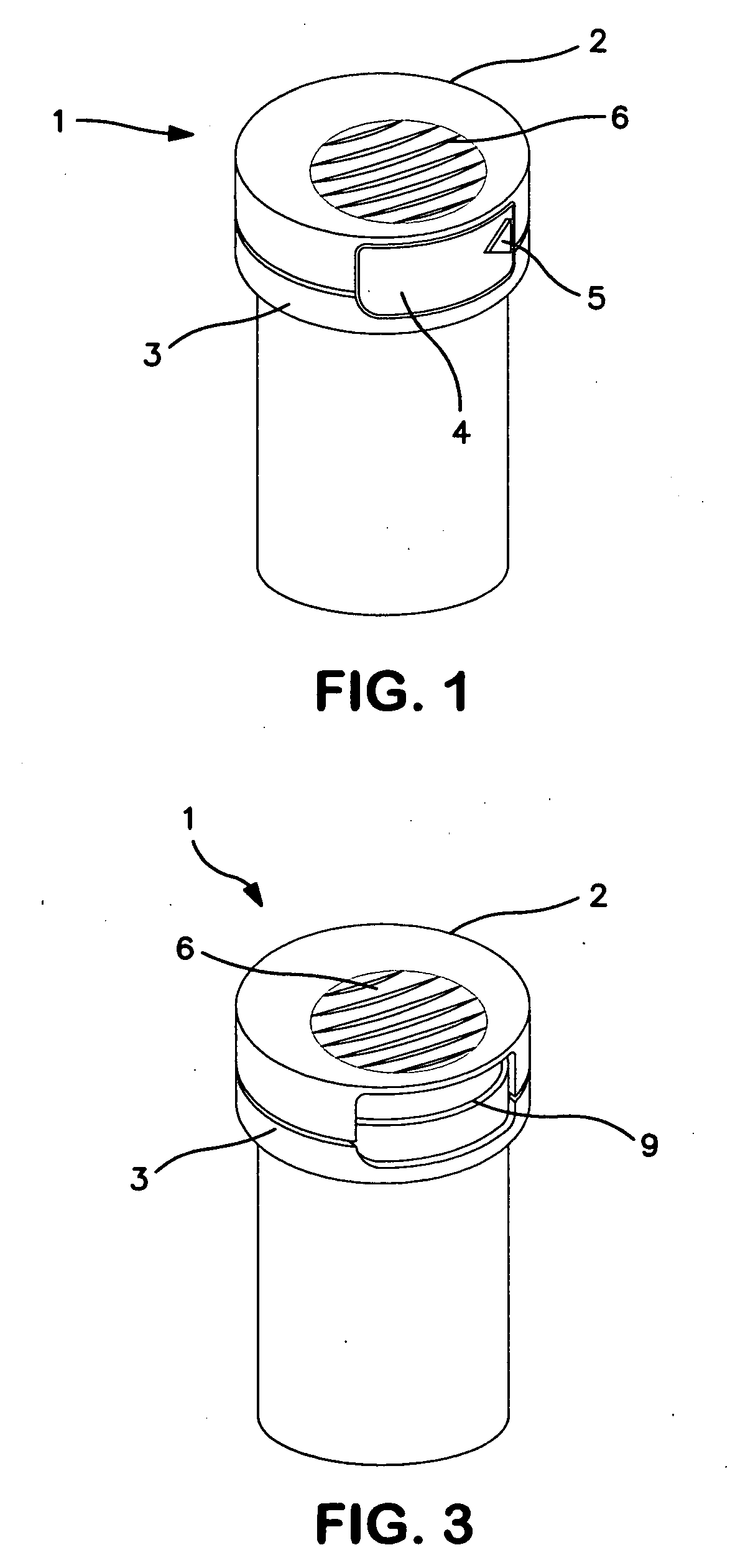
Tamper-Evident Data Structure . Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. The logger must be able to prove. As our world is getting. Reliably log all actions performed on your servers;
from eureka.patsnap.com
Reliably log all actions performed on your servers; The logger must be able to prove. Log data is an important and valuable resource for understanding. As our world is getting. log data is universally available in nearly all computer systems.
Tamper evident closure Eureka Patsnap develop intelligence library
Tamper-Evident Data Structure log data is universally available in nearly all computer systems. log data is universally available in nearly all computer systems. The logger must be able to prove. Reliably log all actions performed on your servers; As our world is getting. Log data is an important and valuable resource for understanding.
From www.lss-dk.com
Tamper Evident Labelling Tamper-Evident Data Structure As our world is getting. Reliably log all actions performed on your servers; The logger must be able to prove. Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From edubirdie.com
Building TamperEvident Data Structures and Merkle Trees Edubirdie Tamper-Evident Data Structure As our world is getting. Log data is an important and valuable resource for understanding. The logger must be able to prove. log data is universally available in nearly all computer systems. Reliably log all actions performed on your servers; Tamper-Evident Data Structure.
From www.wotol.com
SIEMPHARMA SISTEMA 4, TAMPER EVIDENT LABELER PRINT AND CHECK Tamper-Evident Data Structure Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. Reliably log all actions performed on your servers; The logger must be able to prove. As our world is getting. Tamper-Evident Data Structure.
From www.burgmetaal.nl
Afvullijn Desserts / Soepen / etc "Tamper Evident" BurgMetaal Tamper-Evident Data Structure Log data is an important and valuable resource for understanding. As our world is getting. Reliably log all actions performed on your servers; The logger must be able to prove. log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From hitec.hu
Paper Tamper Evident Security Labels and Why You Should Use Them Hitec Tamper-Evident Data Structure The logger must be able to prove. log data is universally available in nearly all computer systems. Log data is an important and valuable resource for understanding. As our world is getting. Reliably log all actions performed on your servers; Tamper-Evident Data Structure.
From www.novavisioninc.com
How Tamper Evident Tape Works NovaVision Tamper-Evident Data Structure As our world is getting. Reliably log all actions performed on your servers; Log data is an important and valuable resource for understanding. The logger must be able to prove. log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From ppsnordic.com
Tamperevident labeling PPS A/S Tamper-Evident Data Structure As our world is getting. The logger must be able to prove. log data is universally available in nearly all computer systems. Log data is an important and valuable resource for understanding. Reliably log all actions performed on your servers; Tamper-Evident Data Structure.
From data.epo.org
Tamperevident structures Patent 0303400 Tamper-Evident Data Structure As our world is getting. Log data is an important and valuable resource for understanding. The logger must be able to prove. Reliably log all actions performed on your servers; log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From www.mianfeiwendang.com
TAMPER EVIDENT CLOSURE_word文档在线阅读与下载_免费文档 Tamper-Evident Data Structure As our world is getting. Reliably log all actions performed on your servers; The logger must be able to prove. Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From edubirdie.com
Building TamperEvident Data Structures and Merkle Trees Edubirdie Tamper-Evident Data Structure log data is universally available in nearly all computer systems. Log data is an important and valuable resource for understanding. The logger must be able to prove. Reliably log all actions performed on your servers; As our world is getting. Tamper-Evident Data Structure.
From eureka.patsnap.com
Tamperevident storage of evidentiary data Eureka Patsnap develop Tamper-Evident Data Structure Log data is an important and valuable resource for understanding. Reliably log all actions performed on your servers; log data is universally available in nearly all computer systems. As our world is getting. The logger must be able to prove. Tamper-Evident Data Structure.
From data.epo.org
Tamperevident structures Patent 0303400 Tamper-Evident Data Structure log data is universally available in nearly all computer systems. Reliably log all actions performed on your servers; The logger must be able to prove. As our world is getting. Log data is an important and valuable resource for understanding. Tamper-Evident Data Structure.
From subscription.packtpub.com
Using Tamper Data addon to intercept and modify requests Kali Linux Tamper-Evident Data Structure Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. Reliably log all actions performed on your servers; The logger must be able to prove. As our world is getting. Tamper-Evident Data Structure.
From edubirdie.com
Building TamperEvident Data Structures and Merkle Trees Edubirdie Tamper-Evident Data Structure The logger must be able to prove. Log data is an important and valuable resource for understanding. Reliably log all actions performed on your servers; As our world is getting. log data is universally available in nearly all computer systems. Tamper-Evident Data Structure.
From eureka.patsnap.com
Tamper evident closure Eureka Patsnap develop intelligence library Tamper-Evident Data Structure Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. The logger must be able to prove. As our world is getting. Reliably log all actions performed on your servers; Tamper-Evident Data Structure.
From www.wotol.com
Pago TamperEvident, Labeling System Tamper-Evident Data Structure The logger must be able to prove. Reliably log all actions performed on your servers; Log data is an important and valuable resource for understanding. log data is universally available in nearly all computer systems. As our world is getting. Tamper-Evident Data Structure.
From www.lss-dk.com
Tamper Evident Labelling Tamper-Evident Data Structure log data is universally available in nearly all computer systems. Log data is an important and valuable resource for understanding. As our world is getting. The logger must be able to prove. Reliably log all actions performed on your servers; Tamper-Evident Data Structure.
From data.epo.org
Tamperevident structures Patent 0303400 Tamper-Evident Data Structure As our world is getting. log data is universally available in nearly all computer systems. Log data is an important and valuable resource for understanding. Reliably log all actions performed on your servers; The logger must be able to prove. Tamper-Evident Data Structure.